Nginx App Protect testing
-
Browse again to the Arcadia web app and verify that it is still working.
-
Let’s simulate a Cross Site Scripting (XSS) attack, and make sure it’s blocked:
https://<INGRESS-EXTERNAL-IP>/?a=%3Cscript%3Ealert(%27xss%27)%3C/script%3E
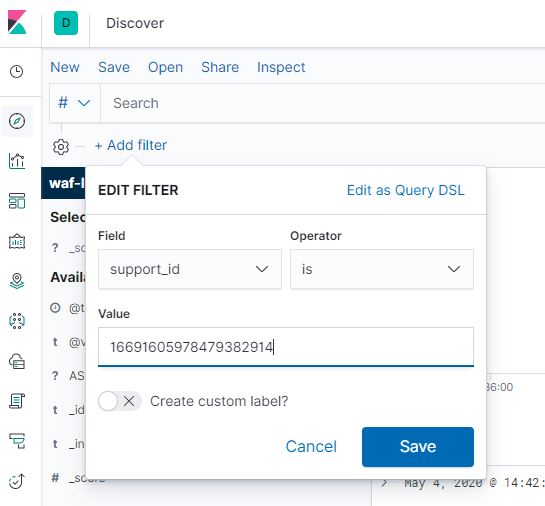
Each of the blocked requests will generate a support ID, save it for later.
- Browse to the ELK as before and click the “Discover” button:
Here, you’ll see all the request logs, allowed and blocked, sent by the Nginx WAF to ELK.
Let’s look for the reason why our attack requests were blocked.
- Add a filter with the support ID you have received as seen bellow:
In the right side of the panel, you can see the full request log and the reason why it was blocked.
- Continue and explore the visualization capabilities of Kibana and log information from Nginx WAF by looking into the next two sections bellow the “Discover” button (Visualize and Dashboard -> Overview).